Abstract
The early identification of COVID-19 is critical to prevent the disease from spreading at the community level. Cloud computing allows healthcare providers to enhance patient care, exchange information more quickly, increase operational efficiency, and save expenses. Thus, this research investigates cloud computing applications in the context of an outbreak. We gathered, summarized, and evaluated scientific papers on cloud computing throughout an outbreak that were released between 2020 and April 2022 for this Systematic Literature Review (SLR). We employed a pre-defined review methodology to examine commonly known electronic datasets. Keywords were used to look for all publications connected to the subject. 18 papers were chosen for this SLR after thoroughly following the research selection method. This review paper offers current state-of-the-art outcomes and methodologies on cloud computing throughout an epidemic, outlining research gaps and providing directions for future research. The results showed that cloud computing plays a crucial role in addressing and relieving side effects in vital situations such as the coronavirus epidemic. We tried to provide a comprehensive study, but non-English articles were not included in this study, so future studies can provide a more comprehensive study by considering all articles in Chinese, Japanese, etc.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
Pneumonia caused by the new coronavirus sickness (COVID-19) in 2019 is a tremendously infectious illness, and WHO has declared the ongoing outbreak a global public health emergency (Cheng et al. 2020). In December 2019, a COVID-19 sickness outbreak erupted in Wuhan, China, and soon spread to other world regions (Chen et al. 2020). COVID-19 is still having a huge influence on the world right now (Rahmani et al. 2021; Zhang 1771). Organizations and corporations have advised their staff to work remotely as a precautionary step in the wake of the COVID-19 epidemic caused by the new Coronavirus. On the other hand, employees have been subjected to many security concerns due to working from home. Furthermore, leaders encounter contradictory problems impacting society and companies, particularly in emerging markets. As a result, becoming a data-driven and technology-enabled high-performance company is both important and urgent. In this scenario, the leading choice for swiftly adopting the cloud paradigm becomes a pillar for enterprises to survive under COVID-19. Furthermore, COVID-19's fast global expansion has enhanced the amount of data collected from numerous sources. Working from home relies heavily on cloud computing services to help staffs do their occupations rapidly and efficiently. In the COVID-19 epidemic catastrophe, the cloud computing environment is an unrecognized hero. It is made up of fast-paced service techniques that mirror the trend of quickly deployable data management apps (Alashhab et al. 2021).
Because the COVID-19 epidemic struck the globe, several industries have migrated to the cloud or intend to do so rapidly. There are several causes why cloud computing is an attractive technology that provides the best way to access Information Technology (IT) software and systems. The phrase "cloud" refers to a cluster of networks in cloud computing. The user has unrestricted access to cloud computing paradigms at any time. Customers often prefer a middleman supplier for Internet service in cloud computing rather than building up their own physical infrastructure (Srivastava and Khan 2018). Cloud computing is an example of a developing technology that provides services independent of time or location, circumvents the constraints of mobile devices to handle large amounts of data, and provides multi-platform compatibility and dynamic provisioning. Computation speed, implementation, energy economy, and integration have all improved. It takes into account client-to-cloud and cloud-to-client authentication, trust, privacy, and security. In order to deliver dependable but effective service soon, it is critical to review and overcome acknowledged issues (Sheth and Tyagi 2022).
Besides, the cloud is the most effective data consumption and management tool. The cloud offers us a wealth of resources through the Internet. Cloud computing systems employ a variety of technologies, each of which has its own set of protocols and procedures. Numerous operations can be executed per second on several servers, but they cannot be executed on their machine. Dryad, Hadoop, and other map-reduce architecture are among the most popular cloud technologies (Alzakholi et al. 2020). It has emerged as a new critical driver for corporate companies seeking to transition into digital enterprises. Remote working is becoming a frequent occurrence across all IT firms, with services available at all times (Gokarna 2021). COVID-19 has made cloud adoption a top priority for the company rather than a gradual change in the future. The advantages of cloud computing include that personnel, particularly engineers, are no longer reliant on a closed hardware-based IT infrastructure, which reduces the need to work from a networked office location. It has created a great demand for competent cloud specialists who can administer and maintain cloud-based systems worldwide (Gokarna 2021).
In order to alleviate physical human demand, technologies are important. As a result, limiting social participation lowers the number of COVID-19 patients. It demonstrates that it is safe for the human generation and humankind as a whole (Prasad et al. 2021). This study aims to solve the issue that no technical solutions can provide a viable response to the imposed lockdown. However, cloud computing has become a hot topic. In the COVID-19 age, an invention like cloud computing could be a cost-effective way for companies to run their IT systems without investing a lot in IT infrastructure development. The writers of this study have attempted to provide some preventative remedies by reviewing several research articles and journals, identifying risk variables, and lowering risk factors. The goal is to identify the major risk issues in the cloud environment and provide a technological solution for logging in and out utilizing the cloud. This paper aims to identify the problems that policymakers have previously faced when dealing with pandemic illnesses, such as COVID-19, and, as a result, new IT capabilities to deal with them. The primary goal of this research is to look into the roles of pay-as-you-go fashion and cloud computing throughout the epidemic. The following is the organization of the paper's structure. Besides, we suggest some directions for future studies. Briefly, the objectives of the paper are:
-
Suggesting a methodical and systematic review of the mechanisms of cloud computing at the time of the pandemic;
-
Suggesting an inductive summary of the selected article;
-
Looking for some basic questions in this domain and indicate the guidelines to encounter the available challenges;
-
Outlining the important areas where the cloud computing mechanisms can be improved.
Finally, the research background is explained below. Then, the systematic method is clearly examined for selecting articles. Selected articles in the method section are totally analyzed in the article review part. The results are presented in Sect. 5. Then open questions and suggestions for future studies are provided. Eventually, Sect. 7 brings the article to a close.
2 Background
This section briefly reviews the literature on cloud computing and its benefits and applications in the COVID-19 era.
Throughout COVID-19, decision-makers recognized the pressing necessity to change their businesses in difficult situations marked by urgency and the need for quick innovation and adaptability. Throughout the COVID-19 epidemic, network and cloud service suppliers are experiencing an unprecedented challenge in meeting end-user requirements. To avoid the transmission of the sickness, several people worldwide have been instructed to stay at home and employ remote connection technology (Abdulsalam and Hossain 2020). Several IT systems and apps that we use daily are being driven by the cloud, which is becoming the new invisible power. We touch many clouds without even realizing it. Giovannetti et al. (2020) used cloud computing in their suggested technique since cloud-based systems are built on a pay-as-you-go pricing mechanism, implying no capacity constraint when utilizing cloud computing. Instead of employing traditional brick-and-mortar-based servers, cloud computing adoption has changed global commercial IT into a new online data storage, administration, and processing approach. This new approach allows users to easily access vast computing capacity over the Internet (Bhardwaj et al. 2021).
According to National Institute of Standards and Technology (NIST), “cloud computing is a model for enabling ubiquitous, convenient, on-demand network access to a shared pool of configurable computing resources that can be rapidly provisioned and released with minimal management effort or service provider interaction” (Madhumitha et al. 2021). It is a digital technology that includes delivering computer system resources like storage, servers, networking, databases, and intelligence through the Internet. This technology allows for speedier innovation and more adaptable resources. Thus, the infrastructure's operating costs are lowered, and the infrastructure's efficiency is improved (Javaid et al. 2020). When it comes to accessibility, cloud computing allows users to access apps and data from anywhere in the globe, on any device with an Internet connection (Bhargav et al. 2021). As shown in Fig. 1, a cloud model is a computational structure with four deployment models, three service models, and five essential features that may be used in a variety of sectors (Hoberg et al. 2012).
Cloud computing mainly has three models, called the service models. SaaS is the most popular service model among its three service types, with customers using it for applications like e-mail, social media apps, word processing, and data storage worldwide. The PaaS paradigm enables customers to install and manage applications built with the provider's programming tools, languages, and services. The PaaS paradigm limits customer control over the underlying cloud infrastructure, while the IaaS model allows them to manage storage, installed applications, operating systems, and some networking components (Weber 2013).
Cloud computing also consists of 4 deployment models, such as:
-
Private cloud A single entity of multiple customers provides the cloud infrastructure with exclusive use.
-
Public cloud The cloud platform is free to utilize and available to the general public.
-
Community cloud A community cloud combines a private cloud and a public cloud. They are multi-tenant systems that allow several companies to collaborate on the same platform.
-
Hybrid cloud The cloud design is made up of three or more autonomous infrastructures (private, communal, or public) that are kept separate but linked together using standardized or customized technologies to facilitate data and device mobility.
The cloud has its own set of distinguishing features and models (Nazneen 2021).
-
On-demand self-service A customer will autonomously give computational facilities arbitrarily, such as server time and network storage without needing human engagement with each service provider.
-
Broad network access Standard frameworks provide access to capabilities throughout the network, allowing diverse thin and thick consumer channels to use (e.g., tablet, laptop, workstation, or mobile phone).
-
Resource pooling The computer resources of the supplier are pooled to accommodate multiple customers utilizing a multi-tenant architecture, with distinct physical and virtual resources dynamically allocated and reallocated based on user requirements. The customer generally has little authority or awareness of the specific location of the services supplied but may define the place at a higher abstraction level, giving the location a sense of freedom (e.g., country, state, or data center). Storage, transmission, memory, and network bandwidth are examples of tools.
-
Rapid elasticity Capabilities may be provided and withdrawn flexibly, and in some circumstances automatically, to readily grow outward and inward in response to demand. The user perceives the capabilities necessary for provisioning to be infinite, and they may be accessed at any time and in any amount.
-
Measured service Using a metering capability at any level of abstraction suitable to the form of operation, cloud systems monitor and maximize resource usage automatically. The utilization of services should be tracked, managed, and recorded, providing both the supplier and the service user with accountability.
3 Methodology
We used Systematic Literature Review (SLR) to guide the literature survey in multiple electronic databases on cloud computing technology to detect, monitor, screen, screen, map hotspots, track, and create awareness to protect and tackle COVID-19, we used Systematic Literature Review (SLR). As previously stated, the goal of this SLR is to find and manifest cloud computing content during an epidemic by asking research questions and choosing appropriate research articles. In conclusion, the purpose of this review is to respond to the following questions:
-
Q1: What are some of the significant new technologies that have been employed to combat COVID-19?
-
Q2: What are the main obstacles policymakers have in dealing with the COVID-19 crisis?
-
Q3: What capacities does cloud computing technology have to handle these issues?
-
Q4: What are the primary challenges for cloud computing technology in the COVID-19 crisis?
Kitchenham’s (2004) recommendations will be followed. Following the recommended method, the following sub-sections are addressed following the review procedure, search strategy procedure, inclusion and exclusion criteria, selecting procedure, and data extraction and synthesis operations.
-
(a)
Review protocol
Following the principles of the SLR by Kitchenham (2004), this method was initialized with developing a comprehensive review protocol. It also improves the consistency of the evaluation. It decreases the researchers’ biases because researchers have to present a search strategy and the criteria for including or excluding any study in the review.
-
(b)
Inclusion and exclusion criteria
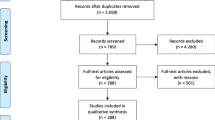
Establishing exclusion and inclusion criteria ensures that only papers related to the research are considered. Research articles from conferences, journals, and cloud computing at an epidemic time in the English language are among our criteria. We looked at research released between January 2020 and April 2022 for this SLR. Only 285 research publications connected to cloud computing were found in our initial search based on keywords during the epidemic of various languages (refer to Fig. 2 for a complete overview of the selection process). We removed publications not obviously relevant to cloud computing in an epidemic era but emerged in the search due to keyword match after a comprehensive assessment of the papers. Publications were also excluded if they were duplicated, didn't have complete text available, or weren't relevant to any of our study topics. We choose peer-reviewed English-language publications. These publications' abstracts and titles were examined. Opinion pieces, non-peer-reviewed publications, incomplete papers, and research is written in languages other than English or without an English translation were also removed.
-
(c)
Search strategy
As illustrated in Fig. 1, the search technique includes both automatic and manual searches. An algorithmic search assisted in discovering primary research and the development of a broader viewpoint. Hence, we widened the scope of the evaluation by including new investigations. The manual search approach was used on the references of the discovered publications following the automated search, as advised by Kitchenham (2004). Scopus, PubMed, Google Scholar, ACM Digital Library, Science Direct, Xplore Digital Library, IEEE, Springer Link, and Wiley Library were the electronic databases studied for an automated search. Although there is a wealth of material accessible in magazines, working papers, books, newspapers, and blogs, we did not choose them for this review article since the notions covered in these sources are not submitted to a review procedure, making their quality unreliable. We used keywords generated from the research questions and the study's title to find research publications. “COVID-19” OR “Pandemic” AND “Cloud computing” AND “Cloud” were utilized in a query for discovering research from the beginning of the COVID-19 epidemic.
After obtaining primary data through search strings, the data analysis stage of the collected research articles commenced by determining their association to the research questions and the study's inclusion and exclusion criteria. Following that, a bibliography management program called Mendeley was employed to store all linked research publications for reference. Mendeley also assisted in the discovery of duplicate research. We combined a manual search with an automated search to ensure we hadn't overlooked anything. Forward and backward referencing were used to accomplish this. Besides, all of the findings were loaded into a spreadsheet for data extraction. Snowballing was used on original publications to extract additional appropriate primary investigations. Snowballing is an incremental procedure in which citations of references are evaluated to uncover more related literature. Subsequently, some preliminary investigations were added to Mendeley as a result of the snowball procedure.
-
(d)
Study selection process
For the eligible studies, a tollgate technique was used (Nidhra et al. 2013). Thus, we used an automated search to retrieve 285 scientific papers after scanning keywords in all appropriate databases. The bulk of the 285 publications was repeated; thus, they were removed. The other 189 articles were subjected to inclusion and exclusion criteria based on title, keywords, abstracts, and publication type. As a consequence, 73 papers were eliminated, leaving 81 studies. The selection criteria were used in the second round, resulting in the exclusion of another 15 research, leaving us with only 20.
After finishing the automatic search step, we began a human search technique to ensure that the search findings were comprehensive. We screened the other 20 papers and looked through the references to see if any relevant research publications had been missed during the computerized search. A manual search yielded two more studies. Following the addition of these papers, a preliminary list of 22 primary publications was generated.
The pre-final selection of 22 papers was then subjected to the quality assessment criteria (QAC). As this is the penultimate phase in determining an ultimate list of publications for SLR, quality evaluation criteria were used at the end. In most cases, QAC finds publications whose quality is insufficient to address the research issue. After using QAC, one research was eliminated, leaving us with 21 main studies. For a detailed step-by-step summary of the selecting procedure, see Fig. 1.
-
(e)
Quality assessment criteria
Kitchenham (2004)’s QAC is founded on the notion of making a judgment based on the overall quality of a series of research. The criteria below were employed to evaluate the quality of chosen investigations. This criterion assisted us in determining the validity of conclusions and picking the most appropriate research articles for our study.
Questions for the quality assessment criteria:
-
Are the subjects given in a research article related to the review article's goals?
-
Is the background of the research described in the research survey?
-
Does the research publication clearly clarify the study approach and methodology?
-
If data collecting is performed in the investigation, is the technique for doing so described?
-
Is the data analysis procedure properly communicated with examples?
In order to ascertain the trustworthiness of a given acknowledged study, we examined 21 chosen papers utilizing the stated quality evaluation questions. Nidhra et al. (2013) inspired these five QA schemata. The survey's quality was assessed based on the results of each QA question. Each question was given two points, and the study's quality was judged picked if it had a score of 5 or more on a scale of 10. Hence, publications with a score of less than 5 were excluded. In the end, 21 papers were chosen for this review article based on this criterion.
-
-
(f)
Data extraction and synthesis
Metadata from chosen research (21) was retrieved throughout this stage. We utilized Mendeley and MS Excel to maintain the information for these investigations, as previously indicated. The major goal of this stage was to keep track of the information gathered during the preliminary research Kitchenham (2004). The data were extracted and entered in an excel file, which included research ID (to identify each study), authors, study title, publishing platform (conference proceedings, journals, etc.), publication year, citation count, and study context (techniques utilized in the study). This information was gathered following a careful examination of each study to determine the investigators' methods and methodology. It also made it easier for us to categorize the research based on the languages in which the approaches were used. Table 1 lists the characteristics of the articles that were chosen.
4 Review
As mentioned in the previous section, 18 articles were identified and chosen according to diverse filters. In this section, we will review the selected articles. According to their subject, the articles are classified into two sections, including cloud computing in the health section and cloud computing in the education section. Based on the analysis of the articles, it was found that cloud computing in the health sector is divided into three parts, including remote monitoring, mobile cloud computing, and maintaining security and privacy in cloud computing (see Fig. 3). After reviewing the articles, a summary of the most important goals and study aids are given in Table 2.
4.1 Cloud computing in healthcare
Cloud-based technologies, which supply data storage and computing resources controlled by external service providers, are increasingly recognized for enhancing healthcare quality, efficiency, and safety. Individual supplier companies have used cloud systems to provide discrete COVID-19-relevant capabilities for organizational and clinical procedures such as monitoring, testing, diagnostics, triage, and consultations (Cresswell et al. 2021). Cloud computing is an emerging concept that brings several advantages to healthcare systems. The following points can be used to describe the advantages: (1) It improves system pace and efficacy; cloud monitoring solutions often handle patient status using a collection of servers, which improves system speed and efficacy. (2) It has a lot of storage space for storing large healthcare data files. (3) It assists in analyzing all patient data and disseminating all data to support and enhance decision-making procedures. (4) It utilizes security layers to protect cloud data from hacking, making it safer than local servers to preserve patient data (El-Rashidy et al. 2020).
In the following, articles related to cloud computing in the health sector will be reviewed. The articles are divided into three sections: remote monitoring, mobile cloud computing, security, and privacy systems.
4.1.1 Remote monitoring
Vital sign monitoring is a crucial part of health management. These signals are crucial to measuring since they frequently provide direct information regarding aberrant physiology. Most medical practices are now ill-equipped to conduct large-scale diagnostic testing. Hence, vital sign monitoring might be used as a criterion for prioritizing tests. Hospital visits for vital sign monitoring, on the other hand, might result in a rise in nosocomial transmission. It is especially critical to protect frontline healthcare personnel. Additionally, an uninfected person's visit to the hospital would enhance their chances of developing an infection. Controlling the transmission chain is essential. Thus, home isolation is recommended for people who have been quarantined and those infected with COVID-19. As a result of the COVID-19 epidemic, there is an urgent necessity to improve remote vital sign monitoring technologies. Because cellphones are so widely used and affordable, camera-based solutions are readily accessible at no additional expense (Rohmetra et al. 2021). Remote monitoring has the potential to improve patient monitoring and management. In the present situation of a worldwide COVID-19 epidemic, when social distance is advocated, and the amount of in-person patient-physician encounters has substantially decreased, the value of remote monitoring has become more obvious. Remote monitoring might be done non-invasively via wearable devices or with continuous pressure monitoring utilizing established algorithms embedded in implanted medical devices (Bekfani et al. 2021). Hence, in this part, articles related to remote monitoring are reviewed.
The primary target of the suggested layout by El-Rashidy et al. (2020) was to close the gap between existing technology and healthcare delivery methods. The wireless body area network, fog computing, cloud computing, and clinical decision support system were all combined to create a whole model for illness diagnosis and prevention. Physicians can help patients with COVID-19 make the best decisions by monitoring them in real-time. The suggested structure is divided into three levels (i.e., a cloud layer, patient layer, and hospital layer). A collection of wearable sensors and a mobile app are used to monitor the patient in the patient layer. Fog network architecture was developed at the cloud layer to address storage and data transmission concerns. Based on the patient’s X-ray scan pictures and transfer learning, they presented a convolutional neural network-based deep learning model for COVID-19 identification in the hospital layer. Compared to the new models, the suggested model produced encouraging outcomes (i.e., the accuracy of 97.95% and specificity of 98.85%). The methodology was a beneficial application, and they predict major impacts on COVID-19 proliferation and a large reduction in healthcare costs.
Dileep and Thogaru (2021) developed a system in which each might have their own personal healthcare companion. It assists individuals in doing regular health checks and producing dynamic health reports on health-related issues they may confront. The healthcare industry generates a great volume of data that must be processed. They discovered the presence of illness using various machine learning methods. Their method was designed to recognize four key diseases: heart and chronic kidney disease utilizing a sequential neural network model, diabetes employing a K-nearest neighbors classification model, and skin cancer utilizing a convolution neural network model. There is a range of IoT-enabled sensors that can recognize detailed information on a patient's human behavior, anatomy, and physiology. As a result of this reality, big data will emerge. The sensors' data is uploaded to the Internet and linked to a cloud server. The patient records might be stored on a website, and therapists could access the information from anywhere on the planet. Any unanticipated alteration in the data of a patient utilizing the healthcare system will almost certainly be uploaded to the relevant doctor with a prompt warning. Rural and isolated regions will benefit the most from this sort of healthcare system.
Ghosh et al. (2021) created the Spatio-temporal knowledge mining framework that models the influence of human movement and other contextual info over vast geographic areas at various time scales. The framework has two primary modules: (1) Spatio-temporal data and computing infrastructure utilizing fog/edge-based structure; and (2) Spatio-temporal data analytics module to efficiently derive knowledge from heterogeneous data sources. Specifically, they created a pandemic-knowledge network to find connections between mobile data and disease transmission and a deep learning structure to forecast the future hotspot zones. They also assisted with home health monitoring using Femtolet and fog/edge-based systems. Empirical assessments demonstrated the efficacy of the presented approaches on real-world datasets linked to COVID-19 in India.
Hasan (2021) demonstrated a novel approach for detecting COVID-19 fever symptoms that relies on IoT-cloud services to address the long time delays in inspecting crowded customers entering public or private agencies, resulting in a risky field for disease propagation. Realistic research was built to offer an autonomously checking approach. Simultaneously, the cloud platform will give a graphical representation of the received data, which can be seen via various monitoring devices. When the system detects a higher temperature that can be regarded as a fever symptom of COVID-19, an SMS message with an alert warning is sent to the monitoring manager and complete client info. The thing speaks cloud displayed the data collected in a graphical form with an excellent and quick reaction.
Ahmad et al. (2021) suggested a technique based on the COVID-19 diagnosing assistant's fuzzy cloud. The suggested technique contains the steps below: registering into the suggested technique, the decision-making process consulting with the public via surveys, patient identification for various areas, level identification of the patient, category wise treatment identification, calculation of fuzzy values for each category, negotiation, and prioritization for protection. Fuzzy cloud-based COVID-19 diagnosis assistant aids in recognizing volunteer specialists for an online interview, master discussion, counting, preparing a direct agreement, addressing preparation, science instruction, conclusion and treatment innovation, and master gathering. They utilized a multi-criterion decision-making technique to identify COVID-19 and also offered therapy based on the patient's state in the suggested technique. It will be extremely beneficial for suspects who are unable to travel to a hospital or clinic. It also avoids unneeded hospital visits in such a dangerous situation. Patients would be able to diagnose themselves using the suggested technique since the suggested system will readily identify all relevant consultations.
Singh and Kolekar (2022) suggested a unique DL approach for COVID-19 diagnostics that can be readily implemented on collaborative edge-cloud computing infrastructure. A fine-tuned transfer learning model based on MobileNet V2 was suggested and trained on chest CT scan pictures. The suggested model beat existing benchmark transfer learning models, with 96.4% accuracy, 98.4% sensitivity, and 0.929 MCC value, respectively, with an average diagnostic time of 43 ms per picture. The recommended architecture was then compressed to an 8 MB size. The optimized layout's dimension was the smallest and most fit for edge implementation compared to the original suggested model and other transfer learning techniques. The empirical findings showed that the suggested model was extremely successful for remote detection of COVID-19 utilizing collaborative edge-cloud computing infrastructures. It might be utilized as a viable replacement for time-consuming clinical diagnostic testing.
Waleed and Elghamrawy (2022) recommended utilizing IoT technology to develop an intelligent cloud-based model for remote monitoring of COVID-19 patients. The cloud-based system component simplifies data storage and processing, which is particularly important given the volume of data generated by ambient assisted living systems, notably for patients with chronic conditions who need more regular readings. Besides, the local element of the system keeps an eye on the patients in case the Internet goes down, or the cloud system fails. The suggested framework employs context-aware approaches to analyze various physiological signs, environmental circumstances, and patient behaviors concurrently. It aims to understand better the COVID-19 sufferer's health state in real-time, as the system will assist clinicians in determining whether the patient has COVID-19 symptoms. Using a case study on a patient with normotensive condition, the findings collected empirically revealed how the suggested approach can efficiently track patients and predict crises properly in unbalanced datasets. Table 2 summarizes the features of the publications under consideration and is supplied at the end of this section for the readers' convenience.
4.1.2 Mobile cloud computing
The number of cellphones accessing the wireless network is rapidly increasing as a result of technological breakthroughs in the ICT domain. Cloud computing and wireless technology advancements have been the driving force behind such rapid growth (Malik et al. 2021). Mobile cloud computing is a popular trending technology that uses cloud features to circumvent the limits of mobile devices. This approach saves battery usage and implementation time by processing mobile applications on a distant cloud server. The most significant benefit of mobile cloud computing is that it minimizes the complexity of the application while also improving the power efficiency of mobile devices (Ramasubbareddy et al. 2021). To make advantage of cloud services, wireless media is used to sustain connectivity across mobile devices and clouds (AlAhmad et al. 2021). This section reviews the articles related to mobile cloud computing in the COVID-19 era.
Rananga and Venter (2020) presented a mobile cloud computing adoption model and illustrated a case scenario in which mobile cloud computing may be beneficial. The researchers were convinced that by embracing the notion of mobile cloud computing, businesses might increase productivity regardless of their geographic location during difficult times like COVID-19 and beyond. These days, one of the most important user needs is mobility. In an ideal world, people would be able to access computer resources at any time, on nearly any device. The advantages of mobile and cloud computing are combined in mobile cloud computing. The complete adoption of the mobile cloud computing idea can either be done instantly or phased in over time, based on companies' location and operational demands.
By creating and successful 72-h deployment of the Honghu hybrid system for COVID-19, Honghu, China, Gong et al. (2020) demonstrated how modern medical informatics technologies might enable effective epidemic containment. The hybrid system was created to gather, integrate, standardize, and analyze COVID-19-relevant data from various sources, including a case reporting system, electronic medical records, diagnostic labs, and mobile social media. The four primary aspects of the Honghu hybrid system are syndromic monitoring on mobile devices, clinical decision support and resource prioritization, policy-making decision assistance, and discharged patient follow-up. The syndromic surveillance element of the Honghu hybrid system encompassed approximately 95% of the population of over 900,000 people. A clinical decision support feature was also added to the Honghu hybrid system to maximize patient care and prioritize precious medical resources.
Popadina et al. (2021) provided the groundwork for a speech analysis system that can recognize COVID-19 patients, particularly those with asthma. Mobile cloud computing and Artificial Intelligence (AI) were utilized to analyze speech characteristics in order to develop an asthma-focused system that could anticipate attacks and recognize COVID-19. They must distinguish between asthma severity and COVID-19 in order to begin appropriate therapy. According to the claimed app, voice snippets were captured regularly and saved in the cloud for rapid and continuous processing and analysis. For evaluating incoming fresh speech signals against a stored database for classifications, a radial basis artificial neural network is constantly accessible.
With COVID-19, Azoui et al. (2021) showed how to develop a flexible and scalable distant ubiquitous health monitoring system for a large number of patients using a novel structure. For remote monitoring of a patient's health, their system combines sensors, wireless connections, service-oriented architecture, and cloud technologies. Each patient is connected to a multitude of sensors in this system. Sensors collect data on the patient's numerous health indicators and deliver it to their own mobile app. The cloud supports remote health monitoring process activities, provides storage resources, and provides computational capacity for assessing and processing patient health data, which is done by the personal mobile application. Therefore, the results proved the usefulness and efficiency of the proposed system. In the continuation of this part, for easier understanding of the readers, Table 3 is presented to summarize the characteristics of the articles under discussion.
4.1.3 Security and privacy
Because the Coronavirus transmits via close social interaction, contact tracking has become critical for halting the virus's transmission. Because of their simplicity of use, broad ownership, and individualized usage, mobile devices are a perfect platform for introducing contact tracing software. However, there is growing concerned about data gathering and usage and data privacy and security (Sowmiya et al. 2021a, b). Because severe cyber-attacks on private and public healthcare services continue, a proposal for a security and privacy strategy to combat pandemic scenarios such as COVID-19 must be made (Ferrag et al. 2021). In this section, the articles related to security and privacy are reviewed.
Tejomurti and Pati (2020) decided how to use the proportionality principle in a cloud-based smart city to preserve COVID-19 patients' privacy rights throughout the epidemic. Additionally, descriptive empirical law was applied in their study. The findings revealed that the proportionality principle is still not well incorporated through regulation and execution in smart cities and cloud computing to preserve positive COVID-19 patients' privacy rights. It is due to people's desire to collect information about positive patients to avoid widespread COVID-19 transmission, regardless of privacy concerns. Hence, it's necessary to evaluate the confidentiality of patient medical records to establish what information should be shared and kept private.
Prasad et al. (2021) investigated and found healthcare technology's security and privacy concerns. They also proposed an architecture called Cloud Computing and Bots Security for COVID-19 Data and Healthcare Management Systems (C2B-SCHMS), which uses a machine learning-based isolation graph to handle anomalies in medical data. They concentrated on the security features of intelligent bots, employing anomaly detection ideas such as long short-term memory and isolation forest. The bots will judge based on the "dataset accessible for analytical purposes" in the cloud environment. As a result, if the genuine/original dataset is accessible, intelligent bots may send the right information to patients, physicians, and other hospital administration personnel without the need for human intervention. Bots will, in turn, stop communicating with stakeholders in the healthcare system until the issue is resolved.
Sowmiya et al. (2021a, b) looked at many contact-tracking applications that used various security and privacy features. They looked at privacy, data storage, and data security in contact-tracing applications in particular. They concluded that the acquired data should be protected using modern encryption standards and random cloud storage. According to the research, users' information would be produced anonymously, encrypted, and protected, and could be sent online and retained only in aggregated form. Contact tracing applications take a centralized or a decentralized method to operate with the user's information. Apps that employ a centralized method pose a significant danger to user privacy.
Akello (2021) looked at potential insider danger to company data as a result of a self-support computing paradigm supported and expedited by the widespread availability of handy, inexpensive, and quickly available cloud-based apps. Shadow IT is a "two-edged sword" in that it provides advantages such as enhanced productivity, job performance, and cost savings while also posing security risks. Furthermore, when established formal organizations of the conventional office, which strengthen data security rules and processes, are weakened with COVID-19 and work from home, vulnerabilities abound. It allows workers more latitude to use unlicensed applications with unvetted risk profiles for work-related tasks, thereby exposing the workplace to risks. They looked at it from the standpoint of the theory of planned conduct and general strain theory, examining it from the viewpoint of a volitional non-malicious insider threat. The experiment is set in a work-from-home environment with COVID-19-related strains. Insider risks, data security, shadow IT, and cloud security are all anticipated to contribute. Their research can combine the idea of planned behavior with the general strain theory to improve explanatory power while addressing one of the theory's noted weaknesses. Table 4 summarizes the main features of the analyzed papers.
4.2 Cloud computing in education
In terms of quality and level, education typically maintains and enhances a country's economic prosperity. In today's educational system, cloud computing is an interesting innovation. The demand for educational institutions and Higher Education (HE) institutions to embrace cloud computing applications has risen due to the COVID-19 epidemic to engage pupils online and conduct research remotely (Bhardwaj et al. 2021). It offers students and educational institutions access to different applications and resources at minimal costs (Madhumitha et al. 2021). In the following, articles related to cloud computing in education are discussed.
Tuli et al. (2020) discussed how better machine learning, mathematical modeling, and cloud computing might assist in anticipating the epidemic's spread in advance. In addition, a case study was provided that demonstrated the severity of COVID-19 spread in nations throughout the world. Their suggested robust Weibull model based on iterative weighting could generate statistically superior forecasts than the baseline. The baseline Gaussian model painted the COVID-19 scenario in an overly positive light.
Madhumitha et al. (2021) investigated the influence of cloud computing on healthcare and how the present COVID-19 epidemic has increased cloud usage in the selected industry. Their study included a qualitative approach, including data obtained from Indian higher education institutes pupils. It was discovered that the majority of pupils are eager to adopt cloud-based learning and that numerous venues have made learning easier and more appealing to pupils. Despite the cloud and its improvements, pupils find it simple and advantageous when utilizing it in their academic studies.
In the COVID-19 pandemic, Alhelou et al. (2021) recognized the significance of cloud computing in boosting the quality of accounting teaching in Palestinian institutions. In the context of the COVID-19 epidemic, the findings show that cloud computing in accounting education allows instructors and pupils to view and recover their data and apps at any time and from any location. It also aids in developing pupils' technological abilities to meet the demands of the labor market.
Bhardwaj et al. (2021) looked at the elements that influence HE organizations in India to adopt cloud computing. In the context of higher education, their research has proposed a unique integrated technology adoption paradigm consisting of the technology-organization environment, technology acceptance model, and diffusion of innovation. This hybrid technology acceptance model-organization environment-diffusion of innovation framework is used in the present investigation to check out eleven hypotheses regarding cloud computing adoption. Confirmatory factor analysis and structural equation modeling were employed to assess them. According to the results, competitive advantage, technology readiness, government backing, technological compatibility, security concerns, senior leadership support, and vendor support are all important factors contributing to Indian public universities adopting cloud computing. According to the report, although the rest of the criteria influence public universities' willingness to use cloud computing, security concerns are a major reason for their apprehension.
Khan et al. (2021) suggested a future educational concept for virtual learning based on cloud computing. They gathered 956 responses from all around Bahrain and analyzed the data with Statistical Product and Service Solutions (SPSS) 25.0. The study discovered that their current school system is unprepared to deal with such a circumstance. Both instructors and students have expressed frustration with the haphazard approach to online learning.
Han and Trimi (2022) investigated the influence and significance of cloud computing in the context of distance learning and education. They performed multiple-case evaluations of 22 online higher education venues in Chinese institutions throughout the outbreak. According to their demands and objectives, the 22 venues used diverse cloud computing models and technologies according to a comparative analysis. The study's findings gave strategic advice to higher education institutions on how to use cloud computing-based platforms for remote instruction, particularly in times of crisis.
The key points of the analyzed articles are summarized in Table 5.
Eighteen selected articles in this section were analyzed in two health and education groups. The key points of the analyzed articles are summarized in Tables 2, 3, 4 and 5. The results show that most of the cloud computing research in the COVID-19 era was done in health. Researchers have tried to remotely monitor and treat patients by designing and providing various frameworks, including mobile cloud computing, wearable sensors, and other smart devices, to prevent patients from accumulating in hospitals and prevent virus expansion. Also, it was found that cloud computing plays an essential role in education. Cloud computing applications have made it possible for users to continue their education remotely and do their homework efficiently at home. However, we have found that while cloud computing has the benefits of reducing costs, reducing distance, and preventing crowds, it does suffer from some disadvantages, including security threats. Future researchers can do more research to reduce cloud computing security threats to use this new technology safely.
5 Discussion
Because all countries are working to stop the virus from spreading, cloud technology can help by offering online services. Cloud-based software provides various advantages to businesses of all sizes, including the flexibility to access software from any device through a native app or a browser. Hence, users may seamlessly transfer their data and preferences from one device to another (Bhargav et al. 2021). Since they do not need the business to acquire extra hardware and may be installed remotely, cloud-based services provide a major advantage to individual companies and specialties: they allow for quick deployment and scaling across various situations (Cresswell et al. 2021). Cloud computing may also be utilized to improve the prediction procedure quickly by employing high-speed calculations. The use of cloud computing technology in the education sector has many benefits, both during the pandemic and after this pandemic end (Kamaludin et al. 2022).
The power industry is interested in cloud computing for a variety of reasons. Cloud computing is a highly efficient and environmentally friendly method of achieving its capabilities. Others represent pricing: cloud computing is quite affordable in financial terms compared to traditional computing methods. Cloud systems are easier to maintain and secure against attack than traditional systems because they can be handled cheaply and with great automation. Eventually, cloud computing provides incredible capacity and elasticity: a contemporary cloud system is frequently hosted on a few data centers, each of which may have more storage, computing, and networking capacity than all of the globe's supercomputing centers combined and can frequently turn on a dime, redeploying services to accommodate rapid load shifts (Annamalai et al. 2019). The article also discusses the commercial advantages of cloud computing (as illustrated in Fig. 4) regarding scalability and flexibility with present software solutions that can be addressed by utilizing cloud platforms and some benefits of adopting cloud platforms during the COVID-19 epidemic.
On the other hand, the outcomes showed that cloud computing enables physicians to stay in touch with their patients and diagnose their health conditions very well during the coronavirus pandemic, where social distancing is of utmost importance (Dadhich 2021). Healthcare organizations should prioritize Low-risk cloud solutions consisting of add-ons to current capabilities. These are more likely to integrate better existing practices than complicated apps connecting individuals and agencies (Cresswell et al. 2021). For example, machine learning and cloud computing can monitor the disease, anticipate pandemic expansion, and develop procedures and programs to control its spread (Tuli et al. 2020). Besides, mobile cloud computing is quickly obtaining traction in the cloud and mobile computing sectors because of its cost-effectiveness and usability (Sadrishojaei et al. 2022). Several businesses may consider cloud-based solutions, like mobile cloud computing, as a viable remedy to the damage caused by the lockdown and beyond (Rananga and Venter 2020; Sadrishojaei et al. 2021).
Cloud computing deployment in healthcare and education during COVID-19 includes options below (Dadhich 2021) (see Fig. 5).
6 Challenges and solutions
COVID-19's fast global expansion has resulted in a rise in data collected from diverse sources. The growing data volume necessitates new data storage systems, storage methods, new locations, and unique technologies, all of which provide a significant problem (Alashhab et al. 2021). Data theft, program run problems, system crashes, low storage capacity, and data loss are just some of the security concerns and issues that can develop in a cloud platform if they are not managed effectively and promptly. For example, mobile devices are a perfect platform for introducing contact tracing software because of their simplicity of use, broad ownership, and individualized usage. As a result, governments, international organizations, and other parties have created several smartphone applications to combat the virus's spread. Nevertheless, there are growing concerns about data gathering, its use, and security (Sowmiya et al. 2021a, b). Moreover, despite the promising solutions supplied by mobile cloud computing in health record monitoring, several obstructions limit mobile cloud computing's primary potential. Privacy and security are the most significant impediments to the use of mobile cloud computing in healthcare, which is a significant research gap (Shabbir et al. 2021). In Fig. 6, some of these key problems are briefly explained (Tanwar et al. 2021).
7 Conclusion
Modern-day technology plays a critical role in the fight against Coronavirus. Because of the present COVID-19 epidemic, people's reliance on cloud computing apps and other technology. Hence, in this research, we studied the roles of pay-as-you-go fashion and cloud computing at the time of the pandemic. 21 papers were selected and analyzed based on diverse filters. Articles were discussed in two groups healthcare and education.
The novel coronavirus is why the current pandemic situation in almost more than 120 nations worldwide declared lockdown to stop spreading the infection. All the companies and the corporate world adopted a new working culture from home. Several nations are battling to protect themselves from the COVID-19 problem, while politicians are confused and unprepared to cope with the situation. The illness and its consequences have made it tough to make the best and most appropriate choices. New IT plays a key role in addressing and relieving stress in such crucial situations as the coronavirus epidemic. COVID-19's impacts are mitigated to a large extent by the technologies. Artificial intelligence, the IoT, cloud computing, robotics, sensor technologies, and other technologies all help reduce the impacts. Cloud computing and storage, among these technologies, is one step forward in terms of contribution. Cloud services are utilized to store, forecast, monitor, and analyze massive patient data. It makes the difficult work of data processing easier and benefits humanity.
Without question, the epidemic issue has influenced nearly every industry, including healthcare, tourism, education, etc. Throughout pandemics, cloud computing can assist in reducing crisis stress and resolving current issues. The health sector is the frontline community responsible for fighting any epidemic, but the technology mentioned will undoubtedly improve their competence and efficiency. The use of cloud computing for crisis management has been explored in the literature; nevertheless, stakeholders' perceptions (patients, nurses, policymakers, and so on) have received less attention. Educational sectors are also stated online classes or electronic learning to continue their course of studies. A cloud computing platform is the only way to accomplish the individual work done. With the increasing cloud computing trend, the related technology is becoming complex to handle huge data sources. And hence the security risk is getting higher day by day, which we have to minimize by properly detecting and providing optimum solutions shortly.
-
Theoretical and practical implications
The present study uses the SLR procedure as the research technique to identify the best available evidence collected from text and opinions in order to provide practical recommendations for policymakers. We also offer several research avenues and provide the groundwork for future experimental applications. These future trends are expected to alter current infrastructure very soon, and the globe will be capable of dealing with similar crises in the future.
Ultimately, we are confident that enough data is being produced globally regarding this pandemic in the form of vast numbers of patients’ profiles, legal frameworks, drug test reports, financial costs, social churning analysis reports, and social reports from medical and economical, and technological experts, and governance. The usage of the aforementioned new technologies would be viable to assist scientists in developing a digital ecosystem to track viral outbreaks, protect the population from infection, and assist people in coexisting with the pandemic in the least amount of time.
-
Directions of research
The COVID-19 epidemic has ushered in a slew of new study avenues for present and future pandemics. The following are some of the most renowned research opportunities.
Contact-less treatment and drug delivery using robotics To limit the interaction of medical personnel with infected individuals, artificial intelligence-based robots can be utilized to make contact-less deliveries and treat patients remotely. Furthermore, the enforced lock-downs have resulted in significant enhancements in air quality across the world.
Data privacy issues The COVID-19 problem has resulted in massive volumes of data being created by many industries' interactions. People are compelled to transmit, utilize, and remove data from the Internet, portable hard drives, or flash memory cards as a result of their ability to work from home. These data transport techniques may not be safe since they may alter or duplicate data or be hacked. There is no backup method for tracking data changes or new data at home. There will be dangers related to the jurisdiction and data loss (Alashhab et al. 2021). Also, a mobile application must be user-centric and safeguard users against unwanted intrusion. Future development will focus on developing an application with strong security and ease of tracing and storing user data. These kinds of measures will provide snoopers and enemies more privacy (Sowmiya et al. 2021a, b). Despite considerable advancements in recent years, cloud-based healthcare apps continue to be underutilized because of their inability to fulfill strict security, privacy, and service quality standards (such as low latency). The edge computing movement and distributed machine learning approach like federated learning has gained traction as a potential option in such situations (Qayyum et al. 2021).
Climate change COVID19-enforced lock-downs have resulted in significant advances in air quality across the world. Nevertheless, there is a prevalent belief that these lockdowns will result in pollution in retaliation. Future research will look at more in-depth analyses of age distributions and demographics with other factors.
Internet quality issues The coronavirus epidemic has had a significant effect on the Internet, and this sudden urgency and requirement have caused certain issues for service providers. It is mirrored in consumers' behavior when using apps at home. These programs often require a fast Internet connection for audio, video quality, and data transfer (Alashhab et al. 2021).
Finally, this study has its limitations, including the fact that non-English articles have been excluded from the study. Future studies can study all articles in all languages.
References
Abdulsalam Y, Hossain MS (2020) Covid-19 networking demand: an auction-based mechanism for automated selection of edge computing services. IEEE Trans Netw Sci Eng. https://doi.org/10.1109/TNSE.2020.3026637
Ahmad S, Mehfuz S, Beg J, Khan NA, Khan AH (2021) Fuzzy cloud based COVID-19 diagnosis assistant for identifying affected cases globally using MCDM. Mater Today Proc. https://doi.org/10.1016/j.matpr.2021.01.240
Akello P (2021) Volitional non-malicious insider threats: at the intersection of COVID-19, WFH and cloud-facilitated shadow-apps
AlAhmad AS, Kahtan H, Alzoubi YI, Ali O, Jaradat A (2021) Mobile cloud computing models security issues: a systematic review. J Netw Comput Appl 190:103152
Alashhab ZR, Anbar M, Singh MM, Leau Y-B, Al-Sai ZA, Alhayja’a SA (2021) Impact of coronavirus pandemic crisis on technologies and cloud computing applications. J Electron Sci Technol 19(1):100059
Alhelou EM, Rashwan A-RM, Abu-Naser SS (2021) The role of using cloud computing in improving the quality of accounting education in palestinian universities in light of the covid-19 pandemic. J Econ Financ Account Stud 3(1):11–32
Alzakholi O, Shukur H, Zebari R, Abas S, Sadeeq M (2020) Comparison among cloud technologies and cloud performance. J Appl Sci Technol Trends 1(2):40–47
Annamalai S, Udendhran R, Vimal S (2019) An intelligent grid network based on cloud computing infrastructures. In: Novel practices and trends in grid and cloud computing. IGI Global, pp 59–73
Azoui A, Idoughi D, Abdelouhab KA (2021) Design of remote pervasive health monitoring system based on cloud computing and SOA. Paper presented at the 2020 2nd International workshop on human-centric smart environments for health and well-being (IHSH)
Bekfani T, Fudim M, Cleland JG, Jorbenadze A, von Haehling S, Lorber A, Rothman AM, Stein K, Abraham WT, Sievert H, Anker SD (2021) A current and future outlook on upcoming technologies in remote monitoring of patients with heart failure. Eur J Heart Fail 23(1):175–185
Bhardwaj AK, Garg L, Garg A, Gajpal Y (2021) E-learning during covid-19 outbreak: cloud computing adoption in Indian public universities. Comput Mater Contin 66:2471–2492
Bhargav A, Thilak B, Narasaraopet I, Kiran C (2021) Development of cloud computing networks for covid’19 datasets which are used for medical assistance 6(1)
Chen H, Guo J, Wang C, Luo F, Yu X, Zhang W, Li J, Zhao D, Xu D, Gong Q, Liao J (2020) Clinical characteristics and intrauterine vertical transmission potential of COVID-19 infection in nine pregnant women: a retrospective review of medical records. Lancet 395(10226):809–815
Cheng Y, Luo R, Wang K, Zhang M, Wang Z, Dong L, Li J, Yao Y, Ge S, Xu G (2020) Kidney disease is associated with in-hospital death of patients with COVID-19. Kidney Int 97(5):829–838
Cresswell K, Williams R, Sheikh A (2021) Using cloud technology in health care during the COVID-19 pandemic. Lancet Digital Health 3(1):e4–e5
Dadhich P (2021) Cloud computing impact on healthcare services during covid-19 pandemic. Int J Res Anal Rev IJRAR 8(1):38–42
Dileep P, Thogaru M (2021) Real time cloud computing based COVID-19 health monitoring system using IOT with integration of machine learning approach to create safety environment. Ann Rom Soc Cell Biol 25:2076–2086
El-Rashidy N, El-Sappagh S, Islam S, El-Bakry HM, Abdelrazek S (2020) End-to-end deep learning framework for coronavirus (COVID-19) detection and monitoring. Electronics 9(9):1439
Ferrag MA, Shu L, Choo K-KR (2021) Fighting COVID-19 and future pandemics with the Internet of Things: security and privacy perspectives. IEEE/CAA J Autom Sin 8(9):1477–1499
Ghosh S, Mukherjee A, Ghosh SK, Buyya R (2021) STOPPAGE: spatio-temporal data driven cloud-fog-edge computing framework for pandemic monitoring and management. arXiv preprint. arXiv:2104.01600
Giovannetti E, Plossky A, Kettani N, Hemmerlein C, Neto G, Martinez J (2020) Economic impact of OTTs on national telecommunication/ICT markets
Gokarna M (2021) Reasons behind growing adoption of cloud after covid-19 pandemic and challenges ahead. arXiv preprint. arXiv:2103.00176
Gong M, Liu L, Sun X, Yang Y, Wang S, Zhu H (2020) Cloud-based system for effective surveillance and control of COVID-19: useful experiences from Hubei. China J Med Internet Res 22(4):e18948
Han H, Trimi S (2022). Cloud computing-based higher education platforms during the COVID-19 pandemic. arXiv preprint. arXiv:2203.03714
Hasan MW (2021) Covid-19 fever symptom detection based on IoT cloud. Int J Electr Comput Eng 11(2):1823
Hoberg P, Wollersheim J, Krcmar H (2012) The business perspective on cloud computing-a literature review of research on cloud computing
Javaid M, Haleem A, Vaishya R, Bahl S, Suman R, Vaish A (2020) Industry 4.0 technologies and their applications in fighting COVID-19 pandemic. Diabetes Metab Syndr Clin Res Rev 14(4):419–422
Kamaludin N, Juanda EA, Abdullah AG (2022) Utilization of cloud computing for learning in the pandemic era of covid 19. Paper presented at the 4th International conference on innovation in engineering and vocational education (ICIEVE 2021)
Khan S, Al-Dmour A, Bali V, Rabbani MR, Thirunavukkarasu K (2021) Cloud computing based futuristic educational model for virtual learning. J Stat Manag Syst 24(2):357–385
Kitchenham B (2004) Procedures for performing systematic reviews. Keele UK Keele University 33(2004):1–26
Madhumitha M, Rajbabu H, Purswani G (2021) Impact of cloud computing in higher education: amidst COVID-19. Utkal Hist Res J 34:83–94
Malik SU, Akram H, Gill SS, Pervaiz H, Malik H (2021) EFFORT: energy efficient framework for offload communication in mobile cloud computing. Softw Pract Exp 51(9):1896–1909
Nazneen F (2021) Cloud computing and the legal arena: digitization of courts during Covid-19
Nidhra S, Yanamadala M, Afzal W, Torkar R (2013) Knowledge transfer challenges and mitigation strategies in global software development: a systematic literature review and industrial validation. Int J Inf Manag 33(2):333–355
Popadina AO, Salah A-M, Jalal K (2021) Voice analysis framework for asthma-COVID-19 early diagnosis and prediction: AI-based mobile cloud computing application. Paper presented at the 2021 IEEE Conference of Russian young researchers in electrical and electronic engineering (ElConRus)
Prasad VK, Tanwar S, Bhavsar M (2021) C2B-SCHMS: cloud computing and bots security for COVID-19 data and healthcare management systems. Paper presented at the Proceedings of second international conference on computing, communications, and cyber-security
Qayyum A, Ahmad K, Ahsan MA, Al-Fuqaha A, Qadir J (2021) Collaborative federated learning for healthcare: multi-modal covid-19 diagnosis at the edge. arXiv preprint. arXiv:2101.07511
Rahmani AM, Ali Naqvi R, Hussain Malik M, Malik TS, Sadrishojaei M, Hosseinzadeh M, Al-Musawi A (2021) E-learning development based on internet of things and blockchain technology during COVID-19 pandemic. Mathematics 9(24):3151
Ramasubbareddy S, Swetha E, Luhach AK, Srinivas TAS (2021) A multi-objective genetic algorithm-based resource scheduling in mobile cloud computing. Int J Cogn Inform Nat Intell (IJCINI) 15(3):58–73
Rananga N, Venter H (2020) Mobile cloud computing adoption model as a feasible response to countries’ lockdown as a result of the COVID-19 outbreak and beyond. Paper presented at the 2020 IEEE conference on e-Learning, e-Management and e-Services (IC3e)
Rohmetra H, Raghunath N, Narang P, Chamola V, Guizani M, Lakkaniga NR (2021) AI-enabled remote monitoring of vital signs for COVID-19: methods, prospects and challenges. Computing. https://doi.org/10.1007/s00607-021-00937-7
Sadrishojaei M, Navimipour NJ, Reshadi M, Hosseinzadeh M (2021) A new preventive routing method based on clustering and location prediction in the mobile internet of things. IEEE Internet Things J 8:10652–10664
Sadrishojaei M, Navimipour NJ, Reshadi M, Hosseinzadeh M (2022) A new clustering-based routing method in the mobile internet of things using a krill herd algorithm. Cluster Comput 25(1):351–361
Shabbir M, Shabbir A, Iwendi C, Javed AR, Rizwan M, Herencsar N, Lin JC-W (2021) Enhancing security of health information using modular encryption standard in mobile cloud computing. IEEE Access 9:8820–8834
Sheth HSK, Tyagi AK (2022) Mobile cloud computing: issues, applications and scope in COVID-19. Paper presented at the International conference on intelligent systems design and applications
Singh VK, Kolekar MH (2022) Deep learning empowered COVID-19 diagnosis using chest CT scan images for collaborative edge-cloud computing platform. Multimed Tools Appl 81(1):3–30
Sowmiya B, Abhijith V, Sudersan S, Sakthi Jaya Sundar R, Thangavel M, Varalakshmi P (2021) A survey on security and privacy issues in contact tracing application of COVID-19. SN Comput Sci 2(3):1–11
Sowmiya B, Abhijith V, Sudersan S, Sundar RSJ, Thangavel M, Varalakshmi P (2021b) A survey on security and privacy issues in contact tracing application of Covid-19. SN Comput Sci 2(3):1–11
Srivastava P, Khan R (2018) A review paper on cloud computing. Int J Adv Res Comput Sci Softw Eng 8(6):17–20
Tanwar AS, Evangelatos N, Venne J, Ogilvie LA, Satyamoorthy K, Brand A (2021) Global open health data cooperatives cloud in an era of COVID-19 and planetary health. Omics J Integr Biol 25(3):169–175
Tejomurti K, Pati UK (2020) The principle of proportionality in using smart city cloud computing for patients privacy rights protection in handling the Covid-19 pandemic. Solid State Technol 63(4):1117–1123
Tuli S, Tuli S, Tuli R, Gill SS (2020) Predicting the growth and trend of COVID-19 pandemic using machine learning and cloud computing. Internet Things 11:100222
Waleed A, Elghamrawy SM (2022) An intelligent cloud computing context-aware model for remote monitoring COVID-19 patients using IoT technology. In: Advances in data science and intelligent data communication technologies for COVID-19. Springer, pp 197–219
Weber AS (2013) Cloud computing in education ubiquitous and mobile learning in the digital age. Springer, pp 19–36
Zhang J (1771) At present, COVID-19 is still having an enormous impact in global areas. International or long-distance travels are still risky. In consideration of the safety of all speakers and participants, 2nd International conference on international conference on artificial intelligence and cloud computing (ICAICC2020), organized by Yaseen academy, Wuhan, China, had been held online via Tencent Meeting at Dec, 19, 2020. Paper presented at the Journal of Physics: Conference Series
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Zhao, S., Miao, J., Zhao, J. et al. A comprehensive and systematic review of the banking systems based on pay-as-you-go payment fashion and cloud computing in the pandemic era. Inf Syst E-Bus Manage (2023). https://doi.org/10.1007/s10257-022-00617-9
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10257-022-00617-9